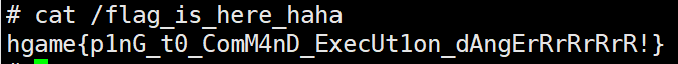[{
"id": "ba1van4",
"intro": "21级 / 不会Re / 不会美工 / 活在梦里 / 喜欢做不会的事情 / ◼◻粉",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=kSt5er0OQMXROy28nzTia0A&s=640",
"url": "https://ba1van4.icu"
}, {
"id": "yolande",
"intro": "21级 / 非常菜的密码手 / 很懒的摸鱼爱好者,有点呆,想学点别的但是一直开摆",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=rY328VIqDc7lNtujYic8JxA&s=640",
"url": "https://y01and3.github.io/"
}, {
"id": "t0hka",
"intro": "21级 / 日常自闭的Re手",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=EYNwm1PQe8o5OcghFb4zfw&s=640",
"url": "https://blog.t0hka.top/"
}, {
"id": "h4kuy4",
"intro": "21级 / 菜鸡pwn手 / 又菜又爱摆",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=BmACniaibVb6IL6LiaYF4Uvlw&s=640",
"url": "https://hakuya.work"
}, {
"id": "kabuto",
"intro": "21级web / cat../../../../f*",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=oPn2ez6Nq12GqPZG6cV7nw&s=640",
"url": "https://www.bilibili.com/video/BV1GJ411x7h7/"
}, {
"id": "R1esbyfe",
"intro": "21级 / 爱好歪脖 / 究极咸鱼一条 / 热爱幻想 / 喜欢窥屏水群",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=FLyUHP6nYov19gA0ia83u8Q&s=640",
"url": "https://r1esbyfe.top/"
}, {
"id": "tr0uble",
"intro": "21级 / 喜欢肝原神的密码手",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=bgcib3gBjJGdKEf7BZ512Uw&s=640",
"url": "https://clingm.top"
}, {
"id": "Roam",
"intro": "21级 / 入门级crypto",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=5wzr9TVyw2nxOz5Jb7ceaQ&s=640",
"url": "#"
}, {
"id": "Potat0",
"intro": "20级 / 摆烂网管 / DN42爱好者",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=NicTy1CDqeHsgzbZEIUU2wg&s=640",
"url": "https://potat0.cc/"
}, {
"id": "Summer",
"intro": "20级 / 歪脖手 / 想学运维 / 发呆业务爱好者",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=4y6zxTBSB3cbseeyPvQWng&s=640",
"url": "https://blog.m1dsummer.top"
}, {
"id": "chuj",
"intro": "20级 / 已退休不再参与大多数赛事 / 不好好学习,生活中就会多出许多魔法和奇迹",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=aM4tJSQSxB5gcauIMDEtUg&s=640",
"url": "https://cjovi.icu"
}, {
"id": "4nsw3r",
"intro": "20级会长 / re / 不会pwn",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=j3LOiav9IluKSYg1VEibblZw&s=640",
"url": "https://4nsw3r.top/"
}, {
"id": "4ctue",
"intro": "20级 / 可能是IOT的MISC手 / 可能是美工 / 废物晚期",
"avatar": "../../images/avatar/4ctue.jpg",
"url": "#"
}, {
"id": "0wl",
"intro": "20级 / Re手 / 菜",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=06FRYslcuprt59OxibicdhqQ&s=640",
"url": "https://0wl-alt.github.io"
}, {
"id": "At0m",
"intro": "20级 / web / 想学iot",
"avatar": "../../images/avatar/at0m.png",
"url": "https://homeboyc.cn/"
}, {
"id": "ChenMoFeiJin",
"intro": "20级 / Crypto / 摸鱼学代师",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=5xyCaLib3lovjrUzf5pWxDQ&s=640",
"url": "https://chenmofeijin.top"
}, {
"id": "Klrin",
"intro": "20级 / WEB / 菜的抠脚 / 想学GO",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=nnzEWNwxMS88jKYre5fOjg&s=640",
"url": "https://blog.mjclouds.com/"
}, {
"id": "ek1ng",
"intro": "20级 / Web / 还在努力",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=pJFuHEqNaFk1If1STvRibWw&s=640",
"url": "https://ek1ng.com"
}, {
"id": "latt1ce",
"intro": "20级 / Crypto&BlockChain / Plz V me 50 eth",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=EmPiaz7Msgg7iaia9tibibjdUyw&s=640",
"url": "https://lee-tc.github.io/"
}, {
"id": "Ac4ae0",
"intro": "*级 / 被拐卖来接盘的格子 / 不可以乱涂乱画哦",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=EI7A02PYs5WUVFP2bciad8w&s=640",
"url": "https://twitter.com/LAttic1ng"
}, {
"id": "Akira",
"intro": "19级 / 不会web / 半吊子运维 / 今天您漏油了吗",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=ku1vqyI1hLJr61PGIlic7Ow&s=640",
"url": "https://4kr.top"
}, {
"id": "qz",
"intro": "19级 / 摸鱼美工 / 学习图形学、渲染ing",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=q5qVDcvyzxee4qiays52mibA&s=640",
"url": "https://fl0.top/"
}, {
"id": "Liki4",
"intro": "19级 / 脖子笔直歪脖手",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=E3j3BJrsAfyl1arfnFKufQ&s=640",
"url": "https://github.com/Liki4"
}, {
"id": "0x4qE",
"intro": "19级 / </p><p>Web",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=K7icYial1VVzlNl7hrD9MlNw&s=640",
"url": "https://github.com/0x4qE"
}, {
"id": "xi4oyu",
"intro": "19级 / 骨瘦如柴的胖手",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=JfeMY6Lz5ZU4GmtTV85otQ&s=640",
"url": "https://www.xi4oyu.top/"
}, {
"id": "R3n0",
"intro": "19级 / bin底层选手",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=icY08gnMlXtoYIJ9ib3eJQ2g&s=640",
"url": "https://r3n0.top"
}, {
"id": "m140",
"intro": "19级 / 不会re / dl萌新 / 太弱小了,没有力量 / 想学游戏",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=zt0iccbnGuV8dOpXIYrJgvg&s=640",
"url": "#"
}, {
"id": "Mezone",
"intro": "19级 / 普通的binary爱好者。",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=rDD29iahzzg8AvQX7fdbFPg&s=640",
"url": "#"
}, {
"id": "d1gg12",
"intro": "19级 / 游戏开发 / 🐟粉",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=icawQKtjLcRiaj7scTRBZ9Qw&s=640",
"url": "https://d1g.club"
}, {
"id": "Trotsky",
"intro": "19级 / 半个全栈 / 安卓摸🐟 / P 社玩家 / 🍆粉",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=LiasEshjTXTrNzJjPHVY3Vw&s=640",
"url": "https://altonhe.github.io/"
}, {
"id": "Gamison",
"intro": "19级 / 挖坑不填的web选手",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=0VaAu2go9mvrMXu1ibmKy1g&s=640",
"url": "http://aw.gamison.top"
}, {
"id": "Tinmix",
"intro": "19级会长 / DL爱好者 / web苦手",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=L2EclrAltb7lk3LBPY6oWA&s=640",
"url": "http://poi.ac"
}, {
"id": "RT",
"intro": "19级 / Re手,我手呢?",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=p1TD1qwKfEK8NZExRDqic1A&s=640",
"url": "https://wr-web.github.io"
}, {
"id": "wenzhuan",
"intro": "18 级 / 完全不会安全 / 一个做设计的鸽子美工 / 天天画表情包",
"avatar": "../../images/avatar/wenzhuan.jpg",
"url": "https://wzyxv1n.top/"
}, {
"id": "Cosmos",
"intro": "18级 / 莫得灵魂的开发 / 茄粉 / 作豚 / 米厨",
"avatar": "../../images/avatar/cosmos.jpg",
"url": "https://cosmos.red"
}, {
"id": "Y",
"intro": "18 级 / Bin / Win / 电竞缺乏视力 / 开发太菜 / 只会 C / CSGO 白给选手",
"avatar": "../../images/avatar/Y.jpg",
"url": "https://blog.xyzz.ml:444/"
}, {
"id": "Annevi",
"intro": "18级 / 会点开发的退休web手 / 想学挖洞 / 混吃等死",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=WN9x96MpjSJ3Gc7a3SHtDw&s=640",
"url": "https://annevi.cn"
}, {
"id": "logong",
"intro": "18 级 / 求大佬带我IoT入门 / web太难了只能做做misc维持生计 / 摸🐟",
"avatar": "../../images/avatar/logong.jpg",
"url": "http://logong.vip"
}, {
"id": "Kevin",
"intro": "18 级 / Web / 车万",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=jaXAqywDMbia39e4OfGXicPQ&s=640",
"url": "https://harmless.blue/"
}, {
"id": "LurkNoi",
"intro": "18级 / 会一丢丢crypto / 摸鱼",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=CLTlN5QPS3aI60icIoxGmdQ&s=640",
"url": "#"
}, {
"id": "幼稚园",
"intro": "18级会长 / 二进制安全 / 干拉",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=G2o7mX9RCTkiaCHeEiaJLBwA&s=640",
"url": "https://danisjiang.com"
}, {
"id": "lostflower",
"intro": "18级 / 游戏引擎开发 / 尚有梦想的game maker",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=eQHtN69C2tgM8Ul8PmtTKw&s=640",
"url": "https://r000setta.github.io"
}, {
"id": "Roc826",
"intro": "18 级 / Web 底层选手",
"avatar": "../../images/avatar/Roc826.jpg",
"url": "http://www.roc826.cn/"
}, {
"id": "Seadom",
"intro": "18 级 / Web / 真·菜到超乎想象 / 拼死学(mo)习(yu)中",
"avatar": "../../images/avatar/seadom.png",
"url": "#"
}, {
"id": "ObjectNotFound",
"intro": "18级 / 懂点Web & Misc / 懂点运维 / 正在懂游戏引擎 / 我们联合!",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=yQnkF86Uy6UkZrZmFYLL4g&s=640",
"url": "https://www.zhouweitong.site"
}, {
"id": "Moesang",
"intro": "18 级 / 不擅长 Web / 擅长摸鱼 / 摸鱼!",
"avatar": "../../images/avatar/Moesang.png",
"url": "https://blog.wz22.cc"
}, {
"id": "E99p1ant",
"intro": "18级 / 囊地鼠饲养员 / 写了一个叫 Cardinal 的平台",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=AJQ9RJRCavhSibMZtRq2JOQ&s=640",
"url": "https://github.red/"
}, {
"id": "Michael",
"intro": "18 级 / Java / 会除我佬",
"avatar": "../../images/avatar/Michael.jpg",
"url": "http://michaelsblog.top/"
}, {
"id": "matrixtang",
"intro": "18级 / 编译器工程师( 伪 / 半吊子PL- 静态分析方向",
"avatar": "../../images/avatar/MATRIX.jpg",
"url": "#"
}, {
"id": "r4u",
"intro": "18级 / 不可以摸🐠哦",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=rJCqQv1EzicpDW77nMa5bYw&s=640",
"url": "http://r4u.top/"
}, {
"id": "357",
"intro": "18级 / 并不会web / 端茶送水选手",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=POaV9Y85NiaUcibaETEKTpfw&s=640",
"url": "#"
}, {
"id": "Li4n0",
"intro": "17 级 / Web 安全爱好者 / 半个程序员 / 没有女朋友",
"avatar": "../../images/avatar/li4no.jpg",
"url": "https://blog.0e1.top"
}, {
"id": "迟原静",
"intro": "17级 / Focus on Java Security",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=xyVPFvQ2dWReoBiahd7naSw&s=640",
"url": "#"
}, {
"id": "Ch1p",
"intro": "17 级 / 自称 Bin 手实际啥都不会 / 二次元安全",
"avatar": "../../images/avatar/Chip.jpg",
"url": "http://ch1p.top"
}, {
"id": "f1rry",
"intro": "17 级 / Web",
"avatar": "../../images/avatar/f1rry.png",
"url": "#"
}, {
"id": "mian",
"intro": "17 级 / 业余开发 / 专业摸鱼",
"avatar": "../../images/avatar/mian.jpg",
"url": "https://www.intmian.com"
}, {
"id": "ACce1er4t0r",
"intro": "17级 / 摸鱼ctfer / 依旧在尝试入门bin / 菜鸡研究生+1",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=gRBlwiawx1lF4UkPKh4Liczg&s=640",
"url": "#"
}, {
"id": "MiGo",
"intro": "17级 / 二战人 / 老二次元 / 兴趣驱动生活",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=XzZggL7hDeicLXb2FSic6sfg&s=640",
"url": "https://migoooo.github.io/"
}, {
"id": "BrownFly",
"intro": "17级 / RedTeamer / 字节跳动安全工程师",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=EnNslsFelj9HibuKoNHwmyg&s=640",
"url": "https://brownfly.github.io"
}, {
"id": "Aris",
"intro": "17级/ Key厨 / 腾讯玄武倒水的",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=anjeaJmx1X79Yp1DNxWrRA&s=640",
"url": "https://blog.ar1s.top"
}, {
"id": "hsiaoxychen",
"intro": "17级 / 游戏厂打工仔 / 来深圳找我快活",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=YGiaicyZ3NkWfOoGOlLPWvAw&s=640",
"url": "https://chenxy.me"
}, {
"id": "Lou00",
"intro": "17级 / web / 东南读研",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=fdAMuUicvOObMv3eZC8y0Ew&s=640",
"url": "https://blog.lou00.top"
}, {
"id": "Junier",
"intro": "16 级 / 立志学术的统计er / R / 为楼上的脱单事业做出了贡献",
"avatar": "../../images/avatar/Junier.jpg",
"url": "#"
}, {
"id": "bigmud",
"intro": "16 级会长 / Web 后端 / 会一点点 Web 安全 / 会一丢丢二进制",
"avatar": "../../images/avatar/bigmud.jpg",
"url": "#"
}, {
"id": "NeverMoes",
"intro": "16 级 / Java 福娃 / 上班 996 / 下班 669",
"avatar": "../../images/avatar/nervermoes.jpg",
"url": "#"
}, {
"id": "Sora",
"intro": "16 级 / Web Developer",
"avatar": "../../images/avatar/Sora.jpg",
"url": "https://github.com/Last-Order"
}, {
"id": "fantasyqt",
"intro": "16 级 / 可能会运维 / 摸鱼选手",
"avatar": "../../images/avatar/fantasyqt.jpg",
"url": "http://0x2f.xyz"
}, {
"id": "vvv_347",
"intro": "16 级 / Rev / Windows / Freelancer",
"avatar": "../../images/avatar/vvv_347.png",
"url": "https://vvv-347.space"
}, {
"id": "veritas501",
"intro": "16 级 / Bin / 被迫研狗",
"avatar": "../../images/avatar/veritas501.jpeg",
"url": "https://veritas501.space"
}, {
"id": "LuckyCat",
"intro": "16 级 / Web 🐱 / 现于长亭科技实习",
"avatar": "../../images/avatar/princessprincepal.jpg",
"url": "https://jianshu.com/u/ad5c1e097b84"
}, {
"id": "Ash",
"intro": "16 级 / Java 开发攻城狮 / 996 选手 / 濒临猝死",
"avatar": "../../images/avatar/ash.jpg",
"url": "#"
}, {
"id": "Cyris",
"intro": "16 级 / Web 前端 / 美工 / 阿里云搬砖",
"avatar": "https://cdn.jsdelivr.net/npm/cyris/images/avatar.png",
"url": "https://cyris.moe/"
}, {
"id": "Acaleph",
"intro": "16 级 / Web 前端 / 水母一小只 / 程序员鼓励师 / Cy 来组饥荒!",
"avatar": "../../images/avatar/Acaleph.jpg",
"url": "#"
}, {
"id": "b0lv42",
"intro": "16级 / 大果子 / 毕业1年仍在寻找vidar娘接盘侠",
"avatar": "../../images/avatar/b0lv42.jpg",
"url": "https://b0lv42.github.io/"
}, {
"id": "ngc7293",
"intro": "16 级 / 蟒蛇饲养员 / 高数小王子",
"avatar": "../../images/avatar/ngc7293.jpg",
"url": "https://ngc7292.github.io/"
}, {
"id": "ckj123",
"intro": "16 级 / Web / 菜鸡第一人",
"avatar": "../../images/avatar/ckj123.jpg",
"url": "https://www.ckj123.com"
}, {
"id": "cru5h",
"intro": "16级 / 前web手、现pwn手 / 菜鸡研究生 / scu",
"avatar": "https://thirdqq.qlogo.cn/g?b=sdk&k=5kpiaPnLZ1cWrp0G8O4qHDg&s=640",
"url": "#"
}, {
"id": "xiaoyao52110",
"intro": "16 级 / Bin 打杂 / 他们说菜都是假的,我是真的",
"avatar": "../../images/avatar/xiaoyao52110.jpg",
"url": "#"
}, {
"id": "Undefinedv",
"intro": "15 级网安协会会长 / Web 安全",
"avatar": "../../images/avatar/undefinedv.jpg",
"url": "#"
}, {
"id": "Spine",
"intro": "逆向 / 二进制安全",
"avatar": "../../images/avatar/spine.jpg",
"url": "#"
}, {
"id": "Tata",
"intro": "二进制 CGC 入门水准 / 半吊子爬虫与反爬虫",
"avatar": "../../images/avatar/tata.jpg",
"url": "#"
}, {
"id": "Airbasic",
"intro": "Web 安全 / 长亭科技安服部门 / TSRC 2015 年年度英雄榜第八、2016 年年度英雄榜第十三",
"avatar": "../../images/avatar/airbasic.jpg",
"url": "#"
}, {
"id": "jibo",
"intro": "15 级 / 什么都不会的开发 / 打什么都菜",
"avatar": "../../images/avatar/jibo.jpg",
"url": "#"
}, {
"id": "Processor",
"intro": "15 级 Vidar 会长 / 送分型逆向选手 / 13 段剑纯 / 差点没毕业 / 阿斯巴甜有点甜",
"avatar": "../../images/avatar/Processor.jpeg",
"url": "https://processor.pub/"
}, {
"id": "HeartSky",
"intro": "15 级 / 挖不到洞 / 打不动 CTF / 内网渗透不了 / 工具写不出",
"avatar": "../../images/avatar/heartsky.jpg",
"url": "http://heartsky.info"
}, {
"id": "Minygd",
"intro": "15 级 / 删库跑路熟练工 / 没事儿拍个照 / 企鹅",
"avatar": "../../images/avatar/mingy.jpg",
"url": "#"
}, {
"id": "Yotubird",
"intro": "15 级 / 已入 Python 神教",
"avatar": "../../images/avatar/Yotubird.png",
"url": "#"
}, {
"id": "c014",
"intro": "15 级 / Web 🐶 / 汪汪汪",
"avatar": "../../images/avatar/c014.png",
"url": "#"
}, {
"id": "Explorer",
"intro": "14 级 HDUISA 会长 / 二进制安全 / 曾被 NULL、TD、蓝莲花等拉去凑人数 / 差点没毕业 / 长亭安研",
"avatar": "../../images/avatar/Explorer.jpg",
"url": "#"
}, {
"id": "Aklis",
"intro": "14 级 HDUISA 副会长 / 二次元 / 拼多多安全工程师",
"avatar": "../../images/avatar/aklis.jpg",
"url": "#"
}, {
"id": "Sysorem",
"intro": "14 级网安协会会长 / HDUISA 成员 / Web 安全 / Freebuf 安全社区特约作者 / FSI2015Freebuf 特邀嘉宾",
"avatar": "../../images/avatar/sysorem.jpg",
"url": "#"
}, {
"id": "Hcamael",
"intro": "13 级 / 知道创宇 404 安全研究员 / 现在 Nu1L 划划水 / IoT、Web、二进制漏洞,密码学,区块链都看得懂一点,但啥也不会",
"avatar": "../../images/avatar/hcamael.jpg",
"url": "#"
}, {
"id": "LoRexxar",
"intro": "14 级 / Web 🐶 / 杭电江流儿 / 自走棋主教守门员",
"avatar": "../../images/avatar/lorexxar.jpg",
"url": "https://lorexxar.cn/"
}, {
"id": "A1ex",
"intro": "14 级网安协会副会长 / Web 安全",
"avatar": "../../images/avatar/alex.jpg",
"url": "#"
}, {
"id": "Ahlaman",
"intro": "14 级网安协会副会长 / 无线安全",
"avatar": "../../images/avatar/ahlaman.jpg",
"url": "#"
}, {
"id": "lightless",
"intro": "Web 安全 / 安全工程师 / 半吊子开发 / 半吊子安全研究",
"avatar": "../../images/avatar/lightless.jpg",
"url": "https://lightless.me/"
}, {
"id": "Edward_L",
"intro": "13 级 HDUISA 会长 / Web 安全 / 华为安全部门 / 二进制安全,fuzz,符号执行方向研究",
"avatar": "../../images/avatar/edward_L.jpg",
"url": "#"
}, {
"id": "逆风",
"intro": "13 级菜鸡 / 大数据打杂",
"avatar": "../../images/avatar/deadwind4.jpeg",
"url": "https://github.com/deadwind4"
}, {
"id": "陈斩仙",
"intro": "什么都不会 / 咸鱼研究生 / <del>安恒</del>、<del>长亭</del> / SJTU",
"avatar": "../../images/avatar/chenzhanxian.jpg",
"url": "https://mxgcccc4.github.io/"
}, {
"id": "Eric",
"intro": "渗透 / 人工智能 / 北师大博士在读",
"avatar": "../../images/avatar/eric.jpg",
"url": "https://3riccc.github.io"
}]
|